Introduction
Ever wondered how hackers can steal your bank OTP, listen to your private calls, or even knock millions of people offline in seconds? The answer lies in two invisible signalling protocols – SS7 and GTP – that quietly power every phone call and data session you use.
These protocols are the hidden “language” of mobile networks. You don’t see them, but every time you make a call, send an SMS, or stream Netflix on 5G, your phone is talking in SS7 or GTP.
The catch? Both protocols were built for connectivity, not security. And that design flaw has turned them into prime targets for hackers:
- In the 2G/3G era, SS7 was exploited to spy on people, intercept OTPs, and track phones worldwide.
- In the 4G/5G era, GTP is being hijacked to steal data, crash networks, and commit massive roaming fraud.
And this isn’t just history. Even in 2025, operators still report real SS7 and GTP attacks – from stolen SMS codes to internet outages affecting millions.
This article breaks down:
- What SS7 and GTP are
- How attackers exploit them
- Real-world cases you need to know
- Why the risks are still alive today
- And what defenses telecoms are building to fight back
Part 1: SS7 – The Old Backbone of Telephony
History
SS7 (Signalling System 7) was developed in the 1970s by telecom operators to standardize the way phone networks communicated. Back then, networks were small, centralized, and based on trust.
The goals were simple:
- Set up and tear down telephone calls
- Exchange SMS messages
- Enable roaming between operators
- Provide services like call forwarding, voicemail, and number translation
It was never designed for security — the assumption was: only trusted operators would use SS7.
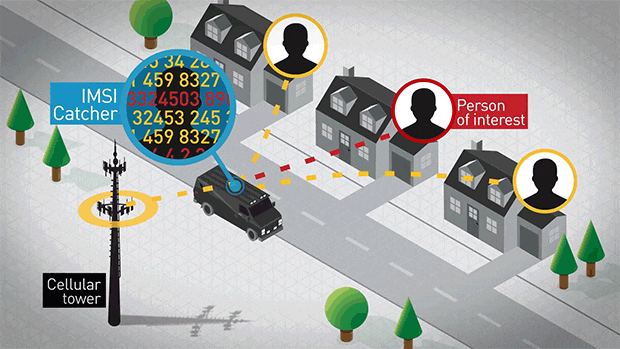
IMSI Captcher is nothing but SS7 Attack tool.
Design Flaws (SS7)
- No Encryption → All signalling travels in plain text.
- No Authentication → Networks don’t verify if requests are genuine.
- Full Trust Model → Once inside, any actor is trusted like a legitimate operator.
Common SS7 Attacks
- Location Tracking → Pinpoint a user’s location by querying cell towers.
- SMS Interception → Redirect OTPs and verification codes.
- Call Interception → Secretly reroute calls for eavesdropping.
- Subscriber Fraud → Fake roaming sessions generate big bills.
- Denial of Service (DoS) → Disconnect users with fake detach requests.
Case Study #1 – German Bank SMS Theft (2017)
- Criminals first infected customers’ computers with malware to steal bank logins.
- When customers tried to transfer money, banks sent SMS OTPs.
- Hackers used SS7 flaws to redirect those OTPs to their own devices.
- They completed fraudulent transfers worth millions of euros.
This was the first large-scale financial crime using SS7.
Case Study #2 – Political Espionage
Intelligence agencies and private contractors have used SS7 to track journalists, activists, and politicians worldwide. With just a phone number, attackers could know your real-time location — without your knowledge.
Why SS7 Still Matters in 2025
Even though many countries are shutting down 2G/3G, SS7 remains active:
- Roaming interconnects → Even 4G/5G calls may fall back to SS7 abroad.
- Legacy SMS services → Many banks still rely on SMS OTPs.
- Developing countries → 2G/3G networks remain widely used.
Result: SS7 continues to be a global security risk.
Part 2: GTP – The Modern Backbone of Internet Data
Introduction
As networks evolved into 3G, 4G, and now 5G, everything shifted from voice/SMS to data-first communication. Calls became VoIP, SMS moved to WhatsApp, and streaming exploded.
To manage this, operators rely on GPRS Tunnelling Protocol (GTP).
What GTP Does
- GTP-C (Control Plane) → Sets up internet sessions and manages mobility when you move between towers or countries.
- GTP-U (User Plane) → Carries your actual data packets (Facebook, YouTube, WhatsApp, Netflix).
Whenever you open YouTube on your phone, a GTP tunnel carries your video packets from the operator’s core to your device.
Design Flaws (GTP)
- Weak Validation → Malicious packets often accepted without checks.
- Trust-Based Roaming → Foreign operator traffic trusted automatically.
- Public Exposure → Misconfigured interfaces exposed to the internet.
Common GTP Attacks
- Subscriber Spoofing → Free internet at the victim’s or operator’s expense.
- Tunnel Hijacking → Inject or steal traffic from live sessions.
- Flooding (DoS) → Overload gateways and cut millions offline.
- Location Tracking → Map subscriber locations via GTP-C queries.
- Billing Fraud → Manipulate roaming charges between operators.
Case Study #3 – BlackHat Conference Demo (2018)
Researchers built a fake roaming network using open-source tools and sent malicious GTP messages to a real operator. They hijacked real subscriber sessions and bypassed billing, proving how cheaply and easily GTP could be abused.
Case Study #4 – Denial of Service Attacks
In multiple regions, attackers flooded GTP traffic, crashing serving gateways (SGWs) and packet gateways (PGWs). Result: millions lost 4G connectivity for hours.
Why GTP Is More Dangerous Than SS7
- Bigger Impact → While SS7 targets individuals, GTP can disrupt entire operators.
- Internet-Scale → Every data session passes through GTP tunnels.
- 5G Dependency → The newest networks still rely on GTP.
In 2025, major mobile operators continue to report roaming fraud and GTP outages affecting millions — proving this is an ongoing, large-scale threat.
SS7 vs GTP – Key Differences
| Protocol | Era | Primary Use | Common Attacks | Impact | Example Case | Who Suffers Most |
| SS7 | 2G/3G | Calls, SMS, roaming | OTP theft, call/SMS interception, location tracking | Individual compromise | German bank OTP theft (2017) | Citizens (privacy & money stolen) |
| GTP | 3G/4G/5G | Data sessions, roaming | Session hijack, DoS, fraud, data theft | Mass disruption | BlackHat demo & operator outages | Operators + millions of users (connectivity loss, fraud) |
Clear Takeaways
For Citizens
- Be cautious with OTPs → Avoid relying solely on SMS-based authentication. Use app-based authenticators (Google Authenticator, Authy) or hardware tokens where possible.
- Stay alert → If your phone suddenly loses service or you miss SMS codes, it could be more than just “network issues.”
- Assume SMS is not private → Never treat text messages as fully secure for sensitive data.
For Operators
- Zero Trust is essential → Never assume foreign or partner networks are safe by default.
- Deploy Protocol Firewalls → SS7 and GTP firewalls must filter malicious signalling traffic in real time.
- Active Monitoring → Continuous anomaly detection and threat intelligence are non-negotiable in 2025.
- Layered Defense → Combine signalling security with subscriber protection (multi-factor authentication, fraud detection systems).
Bottom Line
For citizens, the message is simple: don’t blindly trust SMS-based security. OTPs can be stolen, calls can be intercepted, and your privacy isn’t guaranteed. Use stronger authentication methods whenever possible.
For operators, the responsibility is heavier: zero-trust principles, signalling firewalls, and active monitoring are no longer optional — they’re survival tools. One unfiltered SS7 or GTP message can put millions at risk.
Final Thought
SS7 and GTP were never designed with attackers in mind — yet in 2025, they remain the silent battlefield of global telecom. From stolen OTPs that drain a bank account to GTP floods that crash entire networks, the stakes are higher than ever.
The future of mobile security won’t be decided by shiny apps or faster 5G speeds, but by whether the invisible plumbing of our networks is secured. Until then, every text, every call, and every data session runs through protocols that hackers already know how to exploit.
The question is no longer “Are SS7 and GTP attacks possible?” but “How prepared are we when — not if — they happen again?”
In telecom security, trust is the weakness — and vigilance is the only cure.











