- Platform
- ProductsProducts
- Morphisec for Linux Server Protection
Proactive protection security solution for Linux
- Morphisec for Windows Endpoints
Protective Endpoint Protection
- Morphisec Vulnerability Visibility & Prioritization
Automated Vulnerability Management
- Morphisec for Windows Servers & Workloads
Server & Cloud Protection
- Zimperium MTD
Secure your Mobile Endpoints
- CNAPP + KSPM in CloudWize
Cloud Native Application Protection Platform and Kubernetes Security Posture Management
- CSPM in CloudWize
Cloud Security Posture Management
- CWPP in CloudWize
Cloud Workload Protection Platform
- CASB in CloudWize
Cloud Access Security Broker
- Data Diode
Military Grade Secure One-Way Data Transfer
- Secure Communication Suite
Indigenous secured communication systems
- Risk TM
Digital Risk Monitoring
- Endpoint Protection TM
Platform
- Hunter TM
Protect your ecosystem with Hunter
- Context TM
Cyber Threat Intelligence
- BBM Enterprise
Secure Instant Messaging and Conferencing Platform for your Enterprise
- SecuSUITE
Secure Communications Built for the Future
- CylancePROTECT MOBILE
Prevention-First Mobile Threat Defense Powered by Cylance AI
- Services
Services
- Franchise
- Partners
Partners
- About
- Resources
Resources
Welcome To 63 SATS
Your Own Cyber Security Force (CSF)
Pioneers in Digital Markets and Cybersecurity Excellence

At 63 SATS, we understand that in today's digital landscape, protecting your organization from cyber threats in paramount.That's why we've built a comprehensive suite of products, services, and platforms designed to empower you with the expertise needed to defend against cyber attacks. With 63 SATS by your side, you have your own Cyber Security Force (CSF) ready to safeguard your digital assets and maintain your peace of mind.
Videos
Introducing 63 SATS
Introducing "63 SATS: Your Own Cyber Security Force." Witness the emblem of resilience and vigilance as our logo elegantly unfolds in this captivating reveal.
Our commitment to safeguarding your digital landscape is symbolized in every pixel, reflecting the prowess of a dedicated cybersecurity force.
Welcome to a realm fortified with 63 SATS excellence.

Play Video

Play Video
Introducing CYBX
Introducing our groundbreaking B2C mobile application designed to empower users to assert control over their digital security. Our cybersecurity solution adopts a privacy-centric framework, safeguarding personal data with utmost confidentiality.
Engineered with state-of-the-art technology, this innovative application is tailored to shield individuals from sophisticated persistent threats across diverse domains such as network surveillance, phishing deterrence, and beyond.
Coming Soon...
Platform
End Point
All endpoint devices starting from Laptops, Desktops, Chromebooks, Servers, and Cell Phone Devices are covered with our platform. State of the art technology to prevent all known and unknown malwares and ransomwares attack.
Cloud
Cloud Security to platform for 360 Degree protection from Architecture Design to Runtime, auto scanning and continuous monitoring for vulnerabilities and auto – remediation to fix those findings.
Identity
Leaked Data Breaches, Spoofed Domains, Leaked Login Credentials, and other important digital identities of enterprises can be found with our platform in a dashboard format.
Products
Elevate your cybersecurity defenses with our state-of-the-art products, integrating innovative technology such as polymorphic in-memory protection, real-time risk intelligence, and mobile threat defense with application SDK. Our comprehensive solutions extend to defense-grade secured communications and cloud security, ensuring a robust architecture from inception to runtime. Experience the pinnacle of cybersecurity with our cutting-edge offerings, addressing diverse security needs. From advanced threat detection to secure communication tools, our products empower your cybersecurity posture, providing a holistic and effective shield against evolving digital threats
Morphisec for Windows Endpoints
Every business should be safe from advanced cyber threats, not just the ones with the biggest security budgets.
Morphisec for Windows Servers & Workloads
Servers and cloud workloads are a prime target for hackers. For good reason: your organization’s servers contain the highest value information assets in the entire enterprise. Morphisec Keep proactively prevents the most damaging cyberattacks on your physical and virtual servers with critical exploit prevention and memory protection technology.
Morphisec Vulnerability Visibility & Prioritization
Morphisec Scout automates your vulnerability management by prioritizing those applications your team uses around the clock to ensure you’re not wasting your time, nor your team’s time.
Morphisec for Linux Server Protection
Morphisec Knight for Linux is a proactive protection security solution that shelters your most critical assets by randomizing APIs in memory, stopping supply chain attacks and other exploits at runtime.
Zimperium Maps
The Mobile Application Protection Suite (MAPS) from Zimperium provides four capabilities, including Mobile Application Security Testing (MAST), App Shielding, Key Protection, and Runtime Protection (RASP). The suite provides mobile app teams with centralized threat visibility and comprehensive in-app protection from development through runtime. It combines both inside-out and outside-in security approaches to help organizations build compliant, secure, and resilient mobile apps.
Zimperium Mobile Threat Defense (MTD)
Zimperium Mobile Threat Defense (MTD) – formerly known as zIPS – is a privacy-first application that provides comprehensive mobile security for enterprises. It is designed to protect corporate-owned and/or BYO (bring-your-own) devices from advanced persistent threats across four categories: device, network, phishing, and app attacks.
CASB in CloudWize
CloudWize delivers a single control point for cloud services, including visibility into cloud usage and the ability to detect threats in the cloud.
CWPP in CloudWize
Our vulnerabilities engine allows you to understand CVEs and their exploits and give you full details of remediation steps.
CSPM in CloudWize
CloudWize continuously helps you discover all your assets and risks with a unique graph visualization that you can export.
Secure Communication Suite
Secure communication is when two entities are communicating and do not want a third party to listen in. In order for this to be the case, entities need to communicate in a way unsusceptible to eavesdropping or interception.
Data Diode
Trojan Hunt India’s Data Diode Hardware is the device that guarantees one-wayness of a network connection. With it, you can assure that secrets remain secret, and critical systems are not manipulated.
ContextTM
ContextTM is an intelligence platform to accelerate analysis, prevention, and investigation workflows. Lightning-fast search and data science serve analysts, investigators, SOC/DFIR teams, Risk management, and C-level security executives. With the emergence of new threats and security challenges on a daily basis, it’s now more than ever important to use effective tools to achieve a timely in-depth analysis of any digital threat.
RiskTM
Resecurity provides proactive alerts and comprehensive visibility of internal and external risks targeting the enterprise. Reduce potential blind spots and security gaps with RiskTM.
Endpoint ProtectionTM
Advanced threat detection and monitoring to streamline and secure your cybersecurity environment.
BBM Enterprise
Enterprise-grade Messaging and Conferencing Solution with End-to-end Security and Privacy. BBM® Enterprise offers secure text, voice, video, group chat and conferencing on any device, including smartphones and desktops.
CylanceProtect Mobile
For over a decade, Cylance® AI by BlackBerry has been deployed by businesses and governments around the world, proving its effectiveness in stopping both current and future zero-day attacks with astounding accuracy as validated by leading independent test labs.
SecuSUITE
Secure Messaging and Phone Calls High Security Voice and Messaging for iOS and Android Encrypted Voice and Messaging that’s Intuitive and Efficient
Services
Our expert team offers a variety of cybersecurity services, including risk assessments penetration testing, incident response, and more. We tailor our services to fit your organization’s unique requirements.
Features
Lorem ipsum dolor sit amet,
consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis,
pulvinar dapibus leo. consectetur adipiscing elit.
Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis,
pulvinar dapibus leo. consectetur adipiscing elit.
Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.

The Cybersecurity Imperative in an Era of Global Politics
As I delved into the latest news surrounding cybersecurity, one trend stood out prominently – the alarming surge in attacks on government agencies during the past couple of months. International

Major Data Breaches Shake Corporate Security
Data security is critically vital for all companies, as breaches serve as loud warnings of the consequences of mishandling data. April 2024 saw several significant security incidents. The infographic below

Under Attack: Major Data Breaches and Cyber Incidents That Rocked Global Communities
Explore recent major data breaches & cyber incidents affecting global industries. Learn about breaches from corporations to Government agencies & healthcare provider.

The Great Deception: Beware of ‘Buy Back’ Membership Scams
Beware of ‘Buy Back’ Membership Scams! Sterling Holidays warns against deceptive phone offers, urging vigilance. Verify authenticity & report suspicious activity

Bytes and Battles: Conversations in the Cyber Trenches
Enter the cyber trenches where CISOs clash with hackers in ‘Bytes and Battles.’ A thrilling series unraveling the digital warfare’s clandestine world.

Cyber Attackers Innovate, Evade: Notable Hacker Groups in the News
Stay informed on rising cyber threats. Learn about ToddyCat, ShopifyGUY, and Volt Typhoon, notable hacker groups making headlines in cybercrime.

Cyber Cipher: Decrypting the Cybersecurity Storm
Tech CEO & CISO Neehar Pathare shares insights on cybersecurity challenges: malware, insider threats, nation-state actors, IoT, cloud security, and more. Stay secure!
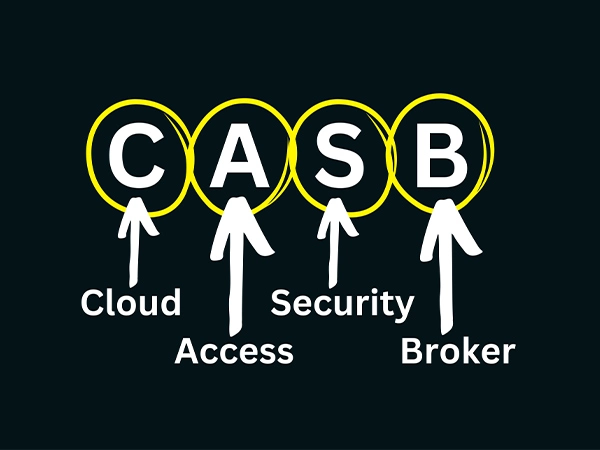
Demystifying CASB in Cyber Security: A Comprehensive Guide
A CASB (Cloud Access Security Broker) emerged as a vital tool in the cyber security. Delve deeper into this article to get a comprehensive overview of CASB.

What is Threat Hunting in Cyber Security? Complete Guide
Threat hunting, a proactive cybersecurity strategy, actively searches for concealed risks that may have evaded conventional security processes. Start defending today!

Automated Moving Target Defence: The Key to Al Attacks
Stay ahead of attackers exploiting. Scrutinize the security of AI-based systems. Learn best practices to protect against evolving threats in cybersecurity.
Defense-in-Depth Layers: The Best Practices for Maximum Protection
Discover why defense-in-depth layers are crucial in today’s threat landscape. Learn best practices for implementation, from training to technology solutions.

Morphisec Fortifies with Next-gen Risk-Based Vulnerability Prioritization
Discover how Morphisec’s advanced Risk-Based Vulnerability Prioritization empowers organizations to effectively patch vulnerabilities & minimize cyber risks.

Measuring Dark Web Intelligence Program Maturity : Key Insights
Discover how to assess the maturity of your company’s dark web intelligence program, mitigate risks, and safeguard your business against cyber threats.

2024 Cyber Threat Landscape Forecast
Discover 2024’s cyber threats analysed by Resecurity’s expert forecast. From ransomware to AI weaponization, anticipate & defend against evolving dangers.

Demystifying DFIR in Cyber Security: Understanding Digital Forensics and Incident Response
Digital Forensics and Incident Response (DFIR) denotes a comprehensive approach to managing cyber threats & security incidents. Explore DFIR in cybersecurity.
See our solutions in action through interactive demos
Get a firsthand experience of how our products and platforms can fortify your defenses against modern cyber threads.





