–And Why You Should Start Paying Attention
Let’s talk about the tech we use every day.
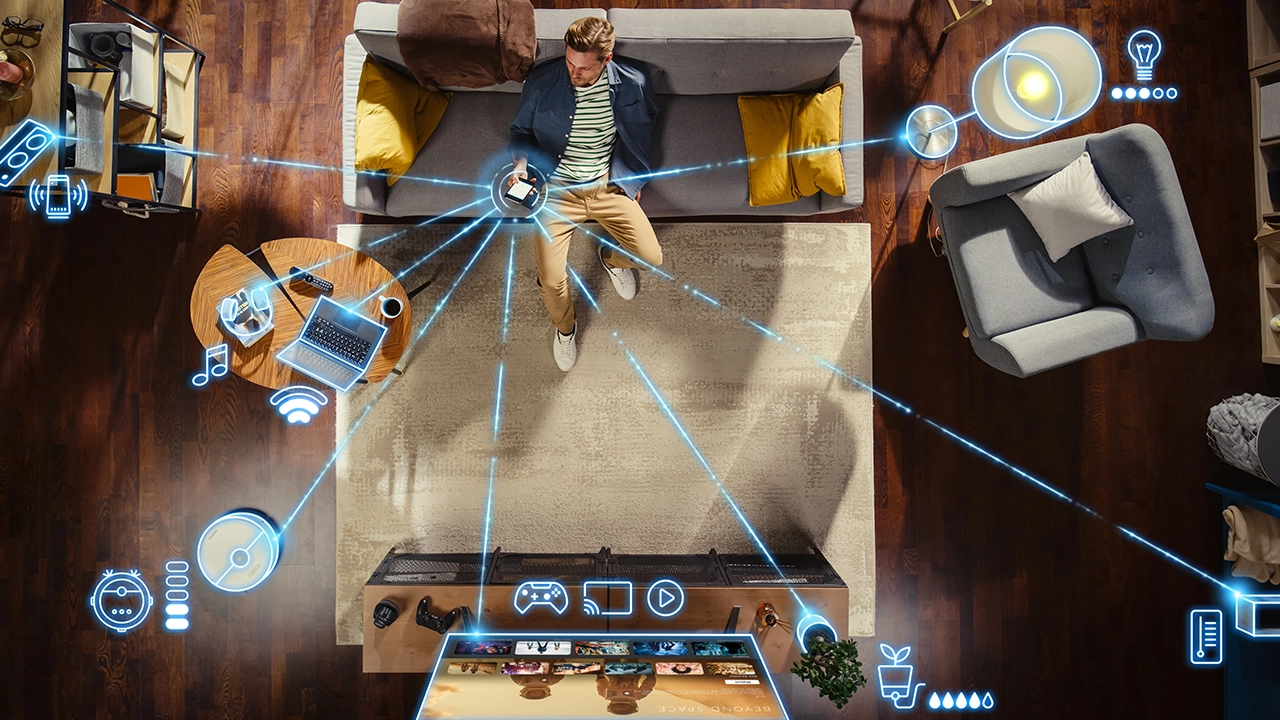
From smartphones and smartwatches to connected TVs and voice assistants, our homes are getting smarter and honestly, it feels like something out of a sci-fi movie.
Your doorbell tells you who’s at the door before they even knock.
Your coffee brews itself.
Lights turn on when you enter.
The thermostat adjusts before you feel the chill.
It’s convenient, seamless, and impressive.
But here’s what we often overlook these smart devices are also collecting data, listening, watching, and sharing information in the background. And in some cases, they can be used against us.
So while smart living makes life easier, it also brings hidden security risks we can’t afford to ignore.
What Are Smart Devices?
Smart devices are everyday tools that connect to the internet and are designed to automate tasks, respond to voice or app commands, and offer remote control. These include smartphones, smart TVs, voice assistants like Alexa, Siri, and Google Assistant, as well as smartwatches, fitness trackers, home security cameras, video doorbells, smart bulbs, plugs, refrigerators, air conditioners, and even keyless car entry systems.
They simplify daily routines and make homes more efficient, but they also come with potential security risks — especially when they’re not properly configured or secured.
“If it’s smart, it’s vulnerable.”
— Mikko Hyppönen, Cybersecurity Expert
You’re Smart Home Might Be Smarter than You Think and that’s the Problem
Smart homes are designed to make life simpler but many of these helpful devices are quietly opening the door to real security threats. And most people don’t even realize it.
Imagine this:
You’re out of town. A hacker remotely disables your smart security system, changes your thermostat settings, and watches your home through your own cameras. It may sound dramatic, but these scenarios are already happening in the real world.
Why Smart Home Attacks Matter:
- Loss of privacy – Strangers could be watching or listening in on personal moments.
- Physical danger – Disabling smart locks or alarms could allow unauthorized entry.
- Loss of control – Malicious actors could manipulate your devices, settings, and even routines.
How to Protect Your Smart Home
You don’t have to give up your smart gadgets — you just have to use them wisely. Here are four easy but critical steps:
- Use strong, unique passwords for each device and app.
- Update firmware and apps regularly to patch known security issues.
- Create a separate Wi-Fi network specifically for smart devices to isolate them from your main devices.
- Enable two-factor authentication (2FA) wherever possible to add another layer of protection.
How Smart Devices Can Become Security Risks
Here’s how smart devices can quietly introduce vulnerabilities into your everyday life:
1. Always-Listening Microphones
Voice assistants are constantly listening for their wake word. But they sometimes activate by mistake and record conversations. If hacked, these devices can be turned into listening tools.
2. Internet-Connected Cameras
Indoor cameras, baby monitors, and doorbell cams can be accessed remotely. Without proper security settings, hackers could watch your home or even speak through your devices.
3. Weak or Default Passwords
Many devices are shipped with simple usernames and passwords. If not changed, they make it incredibly easy for attackers to take control.
4. Over-Permissioned Apps
Some apps request access to your microphone, camera, location, or even contacts — far more than they actually need. If those apps are compromised, so is your data.
This growing reliance on convenience over caution highlights the impact of digital overdependence, where users unknowingly trade privacy and security for ease of use.
5. Outdated Software
Devices that aren’t updated regularly may still contain known vulnerabilities. If manufacturers stop releasing updates — or users ignore them — these flaws stay open to exploitation.
Examples
Example 1: Smart Refrigerator
Use Case:
A Wi-Fi-enabled fridge is connected to your calendar and grocery apps. It uses cameras and AI to track food and send shopping reminders.
Threat:
If compromised, attackers could access private schedules, personal data, or even images inside the fridge to infer your habits — such as when you’re usually not home.
Access to synced calendars allows attackers to predict when a user is away, enabling them to plan physical break-ins or social engineering attacks around upcoming events. Stolen grocery and consumption patterns can reveal personal preferences, health conditions, religious practices, or even income levels — all of which can be exploited for targeted scams or profiling. Internal camera images may disclose household routines, number of residents, or medications stored, contributing further to privacy invasion
Reference:
https://www.iotforall.com/smart-refrigerators-are-more-risky-than-you-realize
https://www.networkbridge.co.uk/blog/is-your-refrigerator-a-security-threat
Example 2: Robotic Vacuum Cleaner (e.g., Roomba)
Use Case:
The vacuum maps your home layout for efficient cleaning using sensors and sends that data to the cloud.
Threat:
If compromised, these devices can leak highly sensitive spatial data — such as floor plans, furniture placement, and room sizes. Some advanced models even capture images or audio to enhance obstacle detection or integrate with voice assistants.
Stolen home maps can be used by attackers to plan physical intrusions with high precision. By identifying entry points, blind spots, and room layout, a criminal can bypass security systems or surveillance blind zones. Additionally, if the vacuum is equipped with a camera or microphone (e.g., for visual navigation or remote assistance), it may be hijacked to secretly capture photos or record conversations.
Furthermore, if the companion app or cloud portal is breached, it could expose not just vacuum data but also location, Wi-Fi credentials, or other connected IoT device profiles, enabling a wider attack surface across the smart home network
Reference:
https://www.abc.net.au/news/2024-10-05/robot-vacuum-deebot-ecovacs-photos-ai/104416632
Example 3: Smart Microwave/Oven
Use Case:
Smart microwaves and ovens are connected to Wi-Fi and controlled via companion apps or voice assistants like Alexa or Google Home. Users can preheat or start cooking remotely, set timers, download cooking instructions from the cloud, and receive notifications about completion or errors.
Threat:
If these appliances are not properly secured, attackers can exploit known vulnerabilities — such as exposed APIs, default credentials, or outdated firmware — to gain remote control. This could allow them to remotely turn on the oven, tamper with temperature settings, or continuously run the appliance, creating potential fire hazards or electrical overloads
Remote control of a smart oven poses both physical safety and cybersecurity risks. On the physical side, unauthorized heating or delayed shutdown can result in kitchen fires, appliance damage, or energy overconsumption — especially if unattended. From a digital perspective, once an attacker gains access to the oven’s firmware or cloud dashboard, they can interact with the broader smart ecosystem. For instance, they could extract Wi-Fi credentials, scan for other connected devices, or hijack the communication channel between the oven and its companion app to deliver malware or perform man-in-the-middle (MITM) attacks. If the appliance integrates with voice assistants, attackers may also be able to abuse voice commands to trigger actions without authentication
Reference:
https://www.bleepingcomputer.com/news/security/is-a-smart-oven-smart-if-it-can-be-hijacked-via-sms
Final Thoughts
Smart devices are here to stay. They make life easier, homes smarter, and routines more efficient. But with that convenience comes a new level of responsibility. Every connected device is a potential doorway — and it’s up to us to make sure that door is locked.
This isn’t about avoiding smart tech. It’s about understanding it.
The more connected your home becomes, the more important it is to secure those connections. By using strong passwords, keeping devices updated, and staying aware of how your data is used, you can enjoy the benefits of smart living — without opening the door to digital threats.