By Shirin Pathare, Chief Relationship Officer [Gov], 63SATS Cybertech
In the high-stakes world of aviation cybersecurity, sophisticated technological defenses form the backbone of digital protection. However, one of the most persistent and underestimated vulnerabilities lies within the human element—where social engineering and insider threats exploit people, not code. As India’s aviation sector rapidly expands, so too does its exposure to these human-centric attack vectors.
While firewalls and encryption protect systems, attackers often bypass them by exploiting trust, distraction, or privilege. Whether it’s a ground staff member unknowingly clicking a phishing link or a disgruntled contractor sabotaging systems, understanding and mitigating human risk is critical for aviation security.
The Art of Deception: Social Engineering in Aviation
Social engineering relies on psychological manipulation to trick individuals into revealing confidential information or performing actions that compromise security. In aviation, these attacks may be physical, digital, or hybrid in nature.
Common Social Engineering Tactics Targeting Aviation:
- Phishing and Spear Phishing: Email or SMS messages posing as IT support, regulatory bodies, or airline vendors. Example: A fake IT alert asks a crew scheduler to “urgently reset” their password via a malicious link.
- Vishing (Voice Phishing): Attackers impersonate air traffic controllers or executives over phone calls. Example: A “senior official” urgently requests flight data access for “safety reasons.”
- Smishing: SMS-based phishing. A message appears to be from the airline’s HR department about a new benefits portal requiring login.
- Pretexting: Attackers create elaborate stories to gain trust. Example: Someone claims to be a maintenance technician with urgent access needs and a plausible backstory.
- Baiting: USB drives or QR codes labeled “Pilot Rosters” or “Confidential Flight Data” left in common areas—tempting staff to plug them in.
- Tailgating/Piggybacking: Unauthorized individuals follow airline staff through secure access points by pretending to be employees who forgot badges.
- Watering Hole Attacks: Compromising websites commonly visited by aviation personnel (e.g., crew portals or airport vendor sites) with embedded malware.
The Enemy Within: Insider Threats in Aviation
Insider threats are uniquely dangerous because they originate from individuals with legitimate access. These threats can be malicious, careless, or compromised:
Types of Insider Threats:
- Malicious Insiders: Employees or contractors with intent to cause harm—e.g., a fired IT admin deletes critical flight systems data.
- Negligent Insiders: Untrained or careless staff—e.g., a flight dispatcher leaves credentials on a sticky note at their workstation.
- Compromised Insiders: Their systems or credentials have been hijacked—e.g., a crew member’s infected tablet spreads malware across airline systems.
Risks at Indian Airports: Human Weak Points
Indian airports, given their size and workforce diversity, face multiple risks related to the human factor:
- Physical Tailgating into secure zones by unauthorized individuals.
- Ground Operations Manipulation: Unauthorized access to flight schedules, fuel information, or baggage systems.
- Fake Maintenance or Vendor Staff: Outsiders posing as legitimate contractors.
- Supply Chain Risks: Compromise of third-party vendors or poorly vetted service providers.
Safeguarding the Skies: Cybersecurity Prevention for Aviation Staff
Key Measures:
- Regular Security Awareness Training: Tailored, realistic scenarios (e.g., mock phishing, pretexting roleplays) across all roles.
- Strict Device and Credential Policies:
- Never share passwords.
- No use of unauthorized USBs or devices.
- No use of unauthorized USBs or devices.
- No use of unauthorized USBs or devices.
- Never share passwords.
- Multi-Factor Authentication (MFA): Enforce MFA for access to operational and passenger data systems.
- Least Privilege & Duty Segregation: Limit access based on role—flight schedulers shouldn’t access HR data; baggage handlers shouldn’t access crew systems.
Real-World Aviation Incidents Involving Human Factors
- Airline X (India, 2023): A phishing attack led to unauthorized access to 15,000 passenger records. The breach originated from a single infected laptop used by outsourced customer support.
- British Airways (2018): Compromised third-party script on their website led to theft of personal and payment data of 500,000 passengers.
- Air India (2021): Data breach involving a third-party IT provider impacted 4.5 million passengers’ personal data.
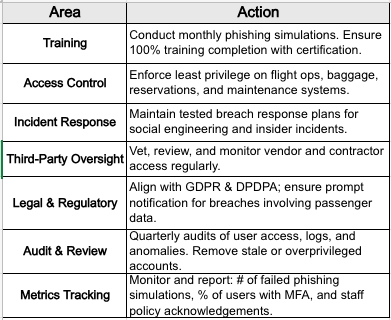
Actionable Checklist for Aviation CISOs & DPOs
Relevant Standards & Frameworks
To reinforce these strategies, aviation security leaders must align their programs with international and national standards:
- ISO/IEC 27001:2022 (Annex A): Controls addressing human security risks.
- NIST Cybersecurity Framework (PR.AT): Focused on personnel security and awareness.
- ISO/IEC 27701 & 29151: Privacy frameworks for managing personal data.
- Regulatory Compliance:
GDPR (EU): Data breach notification within 72 hours.
DPDPA (India): Requires breach disclosure and data fiduciary accountability.
Conclusion: Fortifying the Human Firewall in Indian Aviation
Cybersecurity in aviation is not just about firewalls and encryption—it’s about people. Social engineers and insiders bypass technical defenses by exploiting the human factor. India’s aviation sector, with its scale and complexity, must build resilience into the human layer through training, policy enforcement, cultural awareness, and robust access governance.
By treating people as both a risk and a defensive asset—and aligning with global frameworks—aviation organizations can better protect passenger data, ensure operational continuity, and maintain public trust in the safety of Indian skies.
Next Steps for CISOs & Aviation Leaders:
Begin a 90-day social engineering simulation program.
Audit all third-party access contracts for cybersecurity compliance.
Conduct a cross-functional tabletop exercise focused on insider threat response.
Let’s not wait for the next breach to take the human element seriously.











