In April 2025, Fortinet issued warnings about threat actors maintaining persistent access to FortiOS and FortiProxy devices affected by known vulnerabilities. Around the same time, a threat actor reportedly offered to sell a zero-day exploit targeting FortiGate firewalls. According to cybersecurity firm ThreatMon, who flagged the issue on X, the exploit was advertised on a dark web forum and could allegedly be used to remotely execute code on FortiGate devices—without authentication.
In today’s business world, no organization operates in a vacuum. We rely on vendors, suppliers, and contractors to keep things running smoothly. But every connection brings risk. Just recently, Fortinet made headlines as threat actors were found maintaining persistent access to FortiOS and FortiProxy devices using known vulnerabilities—while another actor allegedly offered a zero-day exploit for FortiGate firewalls on a dark web forum. These aren’t just IT problems—they’re real reminders of how vulnerabilities in third-party systems can open the door to serious cyber threats, regulatory headaches, and reputational harm. That’s why Third-Party Risk Management (TPRM) has become a must-have, not a nice-to-have.
Can you make out what Third Party Risk is?
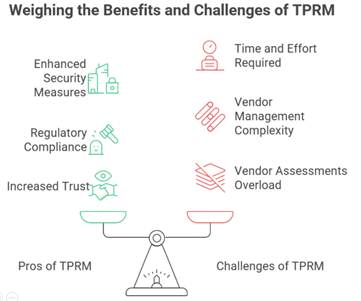
It’s easy to assume that risk lives only within your own systems—but the truth is, every vendor, supplier, or contractor you work with extends your risk footprint. If a partner gets breached, mishandles data, or falls out of compliance, your organization could face the fallout. That’s third-party risk, often hidden but potentially damaging.
Do we need TPRM?
It’s not enough to lock your own doors while leaving the back gate wide open. Third-Party Risk Management (TPRM) gives you the tools to assess, monitor, and manage the risks that come with external partnerships—so you can move forward with confidence, not blind spots.
Think of TPRM as a structured way to stay on top of the risks your third parties, suppliers and vendors might expose you to. It’s more than just ticking boxes during onboarding—it’s an ongoing process that helps you monitor your partners’ security practices, compliance with laws, and overall reliability.
From cloud service providers, logistics partners, and contract staff to software vendors, IT support providers, marketing agencies, payroll processors, data analytics firms, and even facility management teams—if they have access to your systems, data, or customers, they’re part of your risk surface.
Why it matters to regulators
Around the world, regulators are making TPRM a requirement—not just a best practice:
- SEBI in India expects regular risk reviews of critical vendors
- GDPR in Europe demands that your vendors protect personal data just like you do
- ISO 27001:2022 includes supplier controls in its core requirements
Ignoring these expectations could lead to fines, breaches, or worse, loss of trust.
The old way doesn’t work anymore
One-time onboarding assessments won’t cut it in 2025. Threats move too fast. That’s why forward-thinking companies are using AI-driven platforms to:
- Keep a constant eye on vendors’ risk profile
- Send real-time alerts when something changes
- Simulate breach scenarios so teams can prepare
- Align vendor risk with global standards like ISO 27001 and GDPR
This approach turns TPRM from a reactive process into a proactive part of your overall risk strategy.
Understanding TPRM Maturity
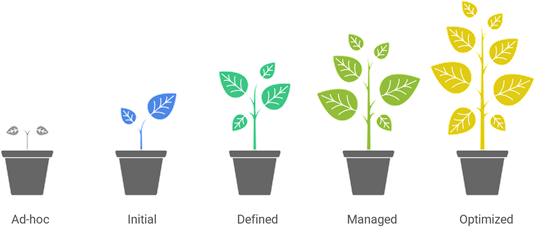
Organizations evolve in how they manage third-party risk, and a maturity model helps benchmark that progress.
- Ad-hoc: No formal TPRM—decisions are reactive and inconsistent.
- Initial: Basic risk assessments start taking shape, often during onboarding.
- Defined: Processes are standardized, documented, and applied organization-wide.
- Managed: Continuous monitoring and proactive mitigation come into play.
- Optimized: TPRM is automated, continuously improving, and tightly integrated into enterprise risk strategies.
5 Stages of a Strong Vendor Risk Program
To build or scale your TPRM efforts, here’s a practical roadmap you can follow:
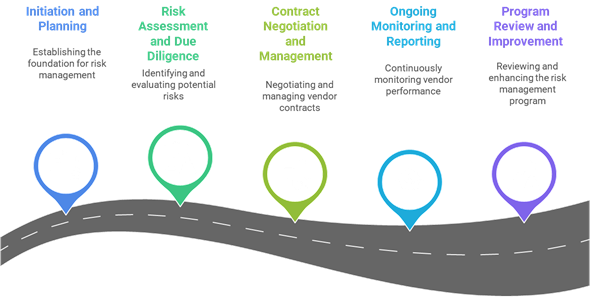
Stage 1: Initiation And Planning – Laying the Groundwork
Start by defining what you’re solving for.
- Clarify goals and scope: Identify high-risk vendors and set measurable objectives.
- Engage stakeholders: Get buy-in from procurement, IT, legal, and business teams.
- Write the policy: Document how you’ll assess, monitor, and respond to vendor risks.
Tip: Prioritize critical vendors and align everyone on responsibilities early.
Stage 2: Risk Assessment & Due Diligence
Understand your vendors before you sign the dotted line.
- Identify risks: Financial, cyber, reputational, operational—get them all on the radar.
- Score and prioritize: Not all vendors are equal—focus on the ones that matter most.
- Do the homework: Use questionnaires, financial reviews, security checks, and background vetting.
Standardized assessments save time and reduce vendor friction.
Stage 3: Contract Negotiation and Management – Contracts with Risk Built-In
Make sure your agreements protect you.
- Include mitigation terms: SLAs, audit rights, indemnities—lock in accountability.
- Track performance: Use a centralized system to manage contracts and renewals.
- Review regularly: Update terms as needs or risks evolve.
Risk-aware contracts = fewer surprises later.
Stage 4: Ongoing Monitoring & Reporting
TPRM isn’t set-it-and-forget-it.
- Monitor performance: Track SLAs and key metrics.
- Watch for new risks: Stay alert to changes like data breaches or regulatory shifts.
- Communicate clearly: Keep leadership and stakeholders informed.
Real-time visibility turns TPRM into a competitive advantage.
Stage 5: Review and Improve
Keep levelling up.
- Measure success: Are your risk goals being met?
- Fill the gaps: Use feedback and audits to tighten weak spots.
- Train and update: Keep your people and policies in sync with changes.
Why This Matters More Than Ever
In 2025, Astra uncovered 5.33 vulnerabilities per minute across assets, including web apps, APIs, cloud setups, and integrated third-party components.
The State of Continuous Pentesting 2025 shows that many critical issues aren’t inside your systems—they’re around them:
- API vulnerabilities led to $2M+ in potential losses
- Cloud misconfigs often stemmed from shared access or third-party tools
- “Low-risk” issues in connected platforms created breach paths most teams never see coming
Third-party risk isn’t theoretical. It’s in the data.
Final thought
Third-party risk isn’t just an IT or procurement issue anymore—it’s a business-wide concern. A weak vendor link can bring your operations to a standstill or land you in regulatory trouble.
A strong TPRM program isn’t just about avoiding risk—it’s about building trust, staying resilient, and being ready for whatever comes next.
http://securityweek.com/threat-actor-allegedly-selling-fortinet-firewall-zero-day-exploit/
https://www.getastra.com/blog/security-audit/penetration-testing-trends/











